I occasionally see love for niche small distros, instead of the major ones…
And it just seems to me like there’s more hurdles than help when it comes to adopting an OS whose users number in the hundreds or dozens. I can understand trying one for fun in a VM, but I prefer sticking to the bigger distros for my daily drivers since the they’ll support more software and not be reliant on upstream sources, and any bugs or other issues are more likely to be documented abd have workarounds/fixes.
So: What distro do you daily drive and why? What drove you to choose it?
I shouldn’t talk because I dip in and out, but I do that because I like the possibilities. Like, what if someone comes up with a concept, but no one tries it, and it turns out to really work? Like, I like immutability as a concept, so I’ve tried Silverblue, Kinoite, and Bazzite. If nobody gave it a go, then the concept would die on the vine.
Also, I like seeing different ways of thinking about technology.
void boots fast on rather old or very low powered copmuters :3
Also on modern firebreathers.
I like runit better than systemd, the packages are current, and it has most of what I want in the main repos.
I also found the documentation excellent in thst it’s a cohesive list of real-world topics rather than a 500-km-deep wiki or forum archive.
I should try a modern Slackware one day. I loved it back before I had broadband and just ordered a burned CD for each new release, but I should try following -current and the Slackbuilds stuff.
Slackbuilds are really nice. Sbopkg lets you download queue files for each program, then automatically install necessary dependencies in the correct order, no matter if they’re available as packages or from source. Unfortunately, Slackware is so bare-bones out of the box that there are still pitfalls. For example, LibreOffice depends on avahi. And to successfully install that, you first need to create an avahi user and group, then install avahi, then write an init script that starts the avahi daemon and another one to stop it on shutdown.
-Current is much too active for my personal taste. I run Slackware because I’m a lazy Slacker.
The laziest approach to Slacking today is to install the default full install, then do:wget https://github.com/sbopkg/sbopkg/releases/download/0.38.2/sbopkg-0.38.2-noarch-1_wsr.tgz #Download the Slackbuilds helper Sbopkg slackpkg install sbopkg-0.38.2-noarch-1_wsr.tgz #Install it sbopkg -r #Sync its local repository to Slackbuilds sqg -a #Build queue files (dependency info) for the repository sbopkg -i flatpak #Install Flatpak and its dependencies flatpak remote-add --user flathub https://dl.flathub.org/repo/flathub.flatpakrepo #Add the Flathub repo
I really like immutable distros, and am currently using NixOS. I feel like despite still being relatively obscure, NixOS is a bit of an outlier since it has more packages than any other distro and is (so far) the only distro I’ve used that has never broken. There is a steep learning curve, and I certainly wouldn’t recommend it for non programmers, but it is something truly different than all mainstream Linux distros while being extremely reliable.
Recently started learning NixOS and seems like it’s going to be ridiculously awesome! Documentation doesn’t look to be great in a lot of areas though unfortunately, so might be a while before I really figure shit out.
Repology artificially reduces the number of packages instead of reporting the actual number. Which I find highly dubious because most packages have a purpose. In particular for repositories like the AUR artificially eliminating packages goes against everything it stands for. Yes it’s supposed to have alternative versions of something, that’s the whole point.
If there wasn’t for this the ranking would be very different. Debian for example maintains over 200k packages in unstable.
I probably should try NixOS, but I’m tempted by BlendOS
I’m using RebeccaBlackOS because it finally utilizes Wayland’s capabilities fully.
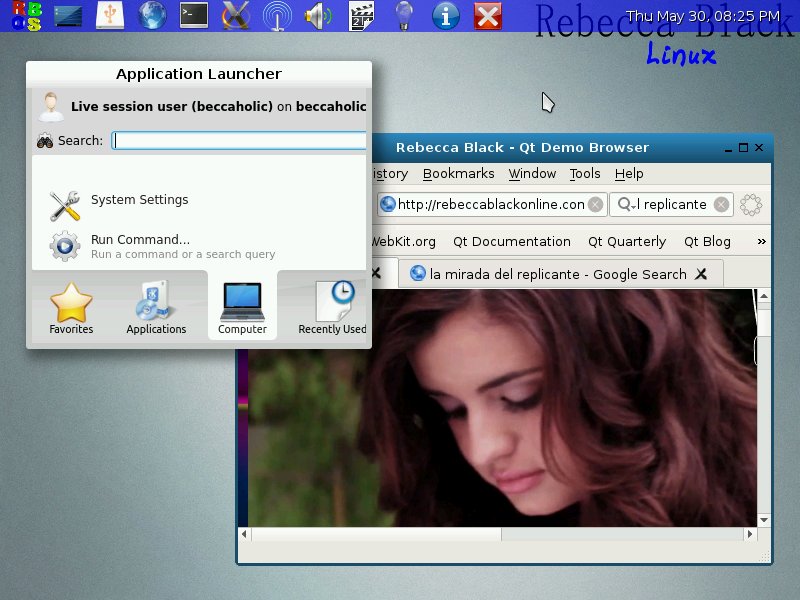
Finally, an OS to rival HannahMontannaOS
It’s Thursday…what the hell are you doing!!! You’re going to break the Internet!!!
I would totally run RebeccaBlackOS or HannahMontannaOS in a vm
The distros are very different. HM is just Ubuntu with a theme.
RB is, to my knowledge, the only distro built around Weston, Wayland’s reference compositor. It doesn’t include any Rebecca Black theming, it’s just called that cause the distro’s maintainer is a fan of hers.Ah ok, good to know
Way back in the day we’d download Britney Spears and My Little Pony™ distros. Times change, I guess.
Breathtaking!
Lmao got worse as I scrolled down.
But xwayland is impressive. I’ve been using i3 but might switch to sway. The xrandr --scale command makes things too fuzzy.
Just saying, I’ve never had a virus with Temple OS.
TCPIP stacks hate this one trick
Actually lol’d
I daily drive Slackware.
What drove me to it was curiosity. “How the fuck does a distro without dependency resolution even work? And why are people still using it?” As it turns out, it’s working very well actually. And I am now one of those people.
I like to tinker and solve puzzles. Installing the most old-fashioned distro on a modern convertible laptop, then bashing it till it looks and feels modern was a fun puzzle.
And it turned out to be a system I can daily drive on any device. Cause contrary to popular belief, you don’t need to hunt down dependencies manually every time you install something, that would be dumb. Once it’s set up, it’s actually very low maintenance and the knowledge I gained about its quirks will likely still be applicable in 10 years.What’s the Slackware way of managing package dependencies, then?
For Slackware itself, you install all available software up front. That way, all dependencies are resolved.
You then just hide the stuff you don’t need from your DE using its menu editor, or ignore it.
During an update, the package manager updates all installed packages, installs all packages that were added to the repo and removes all packages that are obsolete.For additional software, there is a semi-official repo that’s very similar to Arch’s AUR.
And like the AUR, it offers several helper scripts and additional package managers that do dependency resolution.
Or you use Flatpaks.How long do software updates take then, if you’re updating the entire software stack? I can imagine the answer being anywhere from “hours” to “same as the incremental software updates on other distros”
There are very few updates. It’s more stable than Debian. And the repo isn’t huge, maybe twice the size of other distros default installed size.
Cool, thanks. Didn’t realize you can use this neat trick :)
bashing
I see what you did there
Because I’m a software luddite that believe we peaked in design at BSD/Plan9, and most of the “innovations” of enshittified corporate mainstream distros (redhat userland, atomic/immutable environments, “universal” (unless you’re not on linux) package management, containerization of anything and everything) don’t impress me, and more often than not turn me away. I’m not saying software can’t improve, but when it comes to mainstream linux (especially redhat), innovation is always 0 steps forward 40 convoluted leaps back with bonus windows compatibility.
reliant on upstream sources
Not relevant to independent distributions, which I’d actually consider more of a problem with popular distros very often being forks (most often of debian).
I Use Cachyos Its because it has alot of gaming tweaks and optimizations and because installing regular arch is quite painful (yeah its a arch based distro)
I daily drive secureblue; or, to be more precise, its
bluefin-main-userns-hardenedimage.“Why?”, you ask. Because security is my number one priority.
I dismiss other often mentioned hardened systems for the following reasons:
- Qubes OS; my laptop doesn’t satisfy its hardware requirements. Otherwise, this would have been my daily driver.
- Kicksecure; primary reason would be how it’s dependent on backports for security updates.
- Tails; while excellent for protection against forensics, its security model is far from impressive otherwise. It’s not really meant as a daily driver for general use anyways.
- Spectrum OS; heavily inspired by Qubes OS and NixOS, which is a big W. Unfortunately, it’s not ready yet.
I would be really interested in a comparison of Kicksecure and secureblue. I’m interested in running one of them myself
Please allow me to link to an earlier comment of mine that goes over this in more length. You may also find it copied-and-pasted down below:
First of all, apologies for delaying this answer.
Disclaimer:
- I’m not an expert. While I try to verify information and only accept it accordingly, I’m still human. Thus, some falsehoods may have slipped through, my memory may have failed me, and/or what’s found below could be based on outdated data.
- Additionally, I should note that I’m a huge nerd when it comes to ‘immutable’ distros. As a result, I’m very much biased towards secureblue, even if Kicksecure were to address all of their ‘issues’.
- Furthermore, for the sake of brevity, I’ve chosen to stick closely to the OOTB experience. At times, I may have diverged with Qubes OS, but Qubes OS is so far ahead of the others that it’s in a league of its own.
- Finally, it’s important to mention that -ultimately- these three systems are Linux’ finest when it comes to security. In a sense, they’re all winners, each with its use cases based on hardware specifications, threat models, and priorities. However, if forced to rank them, I would order them as:
Qubes OS >> secureblue >~ Kicksecure
Context: Answering this question puts me in a genuinely conflicted position 😅. I have immense respect for the Kicksecure project, its maintainers and/or developers. Their contributions have been invaluable, inspiring many others to pursue similar goals. Unsurprisingly, some of their work is also found in secureblue. So, to me, it feels unappreciative and/or ungrateful to criticize them beyond what I’ve already done. However, I will honor your request for the sake of providing a comprehensive and balanced perspective on the project’s current state and potential areas for improvement.
Considerations: It’s important to approach this critique with nuance. Kicksecure has been around for over a decade, and their initial decisions likely made the most sense when they started. However, the Linux ecosystem has changed dramatically over the last few years, causing some of their choices to age less gracefully. Unfortunately, like most similar projects, there’s insufficient manpower to retroactively redo some of their earlier work. Consequently, many current decisions might be made for pragmatic rather than idealistic reasons. Note that the criticisms raised below lean more towards the idealistic side. If resources allowed, I wouldn’t be surprised if the team would love to address these issues. Finally, it’s worth noting that the project has sound justifications for their decisions. It’s simply not all black and white.
With that out of the way, here’s my additional criticism along with comparisons to Qubes OS and secureblue:
- Late adoption of beneficial security technologies:
Being tied to Debian, while sensible in 2012, now presents a major handicap. Kicksecure is often late to adopt new technologies beneficial for security, such as PipeWire and Wayland. While well-tested products are preferred for security-sensitive systems, PulseAudio and X11 have significant exploits that are absent from PipeWire and Wayland by design. In this case, preferring the known threat over the unproven one is questionable.
- Qubes OS: Its superior security model makes direct comparisons difficult. However, FWIW, Qubes OS defaults for its VMs to Debian and Fedora. The latter of which is known to push new technologies and adopt them first.
- secureblue: Based on Fedora Atomic, therefore it also receives these new technologies first.
- Lack of progress towards a stateless[1] system:
Stateless systems improve security by reducing the attack surface and making the system more predictable and easier to verify. They minimize persistent changes, impeding malware’s ability to maintain a foothold and simplifying system recovery after potential compromises. While this is still relatively unexplored territory, NixOS’s impermanence module is a prominent example.
- Qubes OS: There’s a community-driven step-by-step guide for achieving this.
- secureblue: Based on Fedora Atomic, which has prioritized combating state since its inception[2]. Its immutable design inherently constrains state compared to traditional distros, with ongoing development promising further improvements.
- Deprecation of hardened_malloc:
This security feature, found in GrapheneOS, was long championed by Kicksecure for Linux on desktop. However, they’ve recently chosen to deprecate it.
- Qubes OS: Supports VMs with hardened_malloc enabled OOTB, for which Kicksecure used to be a great candidate.
- secureblue: Continues to support hardened_malloc and has innovatively extended its use to flatpaks.
- This paper provides a comprehensive (albeit slightly outdated) exposition on the matter. Note that it covers more than just this topic, so focus on the relevant parts.
- Colin Walters, a key figure behind Fedora CoreOS and Fedora Atomic, has written an excellent blog post discussing ‘state’.
I have definitely read this answer before. I think we’ve probably already spoken on the matter. Indeed, Lemmy has a serious dearth of users interested and using secure distros over the averages. Thanks for your efforts; I do not know how to follow users on Lemmy but if I did I’d follow you. Do you have a blog/any other forum you’re more active on?
Personally, I find it difficult to justify the time to learn Secureblue (especially the immutable part) or NixOS on Qubes because custom DispVMs with curated salt states work so well already. I’m interested in use-cases that will improve my security but I haven’t found any dialogue on this yet. If you do have opinions on this and know where I can look, I would greatly appreciate it!
I think we’ve probably already spoken on the matter.
That’s definitely possible. Unfortunately, I don’t recall it 😅.
Indeed, Lemmy has a serious dearth of users interested and using secure distros over the averages.
It’s definitely better at this than the platform that starts with an “R” and rhymes with “shit”.
Thanks for your efforts; I do not know how to follow users on Lemmy but if I did I’d follow you. Do you have a blog/any other forum you’re more active on?
That’s such a compliment. This is definitely one of the nicest things I’ve read on Lemmy. I really appreciate it.
Unfortunately, I’m only somewhat active on Lemmy. FWIW, consider checking out the following places if you haven’t yet:
- dataswamp.org/~solene
- privsec.dev
- tech.michaelaltfield.net/
And, of course, Qubes OS’ forums.
Personally, I find it difficult to justify the time to learn Secureblue (especially the immutable part) or NixOS on Qubes because custom DispVMs with curated salt states work so well already. I’m interested in use-cases that will improve my security but I haven’t found any dialogue on this yet. If you do have opinions on this and know where I can look, I would greatly appreciate it!
As I’ve previously alluded to, I don’t have any hands-on experience with Qubes OS yet. So, I don’t think I can contribute meaningfully in this discussion. However, IIRC, there are some discussions found on the forums/discussions page for Qubes OS.
Thanks for the tips
Very interesting had not heard of this one yet. What are the main advantages of using this, that make it more secure?
What are the main advantages of using this, that make it more secure?
More secure compared to your average distro? Or more secure compared to a specific set of distros? Unless, this is properly specified, this comment could become very unwieldy 😅.
Thanks in advance for specifying!
Sorry, it was a badly formatted question I wrote whilst commuting earlier… I ended up looking the project up to look into the details, seems very promising! I’ll soon be booting Linux on a work laptop and think secureblue might be a very strong contender for this 💪
Aight. I’m glad to hear that that has been resolved. I’d love to hear about your experiences on secureblue, so consider to report back. Finally, note that as a hardened distro, some things might work differently from what you’d expect. So be prepared to relearn a thing or two 😉.
I use Nobara on my gaming PC just because it has some gaming tweaks by default but is otherwise just stock Fedora so any issues can be searched as if I was on Fedora.
Declarative system configuration is the killer feature of NiOS. Atomic rollbacks too. Versioning the whole mess in Git, too.
I’d say nix is hardly niche at this point (although I’m biased cause I use it a ton)
There’s even a termux fork these days that runs nix on droid
I use guix because, while it has a small community, the packaging language is one of the easiest I’ve ever used.
Every distro I’ve tried I’ve always run into having to wait on packages or support from someone else. The package transformation scheme like what nixos has is great but Nixlang sucks ass. Being able to do all that in lisp is much preferred.
Plus I like shepherd much more than any of the other process 0’s
As a nix user, guix looks legit nice but it took me until 2 days ago to actually find community projects made for guix(https://whereis.みんな/) . Sometimes I just wish they used the same store and daemon as nix so that nix packages can work as guix dependencies and vice versa.
(Also major thing stopping me from using guix is I don’t get service types at all, let alone how you’d define your own service :( )
You can use nix alongside guix, it’ll just double-up the dependencies on disk:
services (append (list (service nix-service-type)) %base-services)))Services are, in guix terms, any configuration change to a computer, so creating your own service 99% of the time is just extending
etc-service-typeand creating a variable interface to fill in the config file text yourselfCreating a service as in a daemon of some kind uses shepherd and involves extending
shepherd-service-typeorhome-shepherd-service-typewith your service description, depending on whether the service runs in root or user space.Shepherd service configurations aren’t actually part of the guix spec(https://www.gnu.org/software/shepherd/manual/shepherd.html#Defining-Services), but still use Guile, so you can interoperate them super easily.
It’s important in guix to understand lisp pretty thoroughly, and knowing how to program lisp is still a very useful skill to have so I’d recommend learning it even if you never touch guix.
Linux culture is about freedom of choice and movement. Any project can be forked, tweaked, expanded, or outright overhauled by anybody with the know-how in order to meet specific use cases. And those use cases are often the same as other’s use cases. But in most cases, they are still rooted in the project they forked from. I.E, any guide that applies to Ubuntu is likely going to apply to Pop!_OS or Mint, since they’re based on Ubuntu. So there’s rarely a downside to niche distros, because you can have something that’s close enough to a popular distro but that caters to your unique needs and wants.
For me, for example, I use Nobara. It’s rather niche and in most cases, it either works beautifully for you, or it doesn’t work at all, honestly. But it’s based on Fedora, so any guide for Fedora is likely to apply to Nobara. I get all the benefits of being on Fedora with tweaks and patches that make my gaming experience much more stable. And quite frankly, Nobara has made my rig run the best it ever has.
I use Linux since 1999 and I’m with you, I don’t like niche distros. I like them to be well supported with many devs in them, and a structure around them. My days of tinkering died already in 2002 (I’m looking at you Gentoo and sia). Since then, I want things to work the way I expect them. That’s why I now use Debian or Mint.
Same. I started off on Gentoo, jumped to Puppy, jumped to Slack, jumped to Fedora, jumped to Arch, jumped to Nix, jumped to Guix, jumped back to Arch, and now I’m thinking Debian is the only true stable upstream linux needs.
Plus I’m sick of tweaking my configs for the N’th time to work on the M’th system. To quote a random side-character in American Dad: “I have painted my children for the last time.”
(I will at some point start playing with BSD’s though, I just know it. And Haiku too once they have decent laptop support.)
I’m like you, started Linux with v0.99, downloading on floppies at university, installing on 486, installing X11, drivers, etc. It was fun at the beginning, I was young, had time, I was a “LFS” guy, always recompiling everything and all, and it was time consuming, and boring, and slow at the time!!! Then I basically use Debian (Ubuntu, Mint, now MX for 6 years at least) for 20 years… it works, I’m ok with it.
Yes I tried Arch, the low level install, it reminded me of my LFS time, but now I’m an old coot and I don’t have time for this shit 😆
Not sure if niche, but I use Arco Linux instead of the alternatives like Endeavour, Manjaro, or plain arch.
Why? Its easier to setup than straight Arch. Manjaro was all over the place when I tried it a few years back. Arco, right from the ISO stage, let’s you configure exactly what you want, with a handy guide on their website.
But the thing that keeps me loyal is the excellent community. The maintainer himself responds to most of your queries on telegram / discord (not FOSS reeee) and he’s very active on YouTube as well with no nonsense guides and walkthroughs. Shoutout Eric Dubois
Yeah, Erik Dubois and his YT channel were probably the main reasons I stuck with ArcoLinux for as long as I did, even if I did some hopping and eventually ended up on Fedora (I needed a static release)